CISCO Wireless Router :
Wireless Router Solutions: At a Glance
Wireless router solutions today are more advanced, flexible, and secure than ever before.
In the past, the primary job of a wireless router was to extend a hardwired Internet connection or company network securely to wireless-capable computers and handheld devices over radio waves.
In today's challenging business environment, however, many small businesses need more than a traditional wireless router. They need an appliance that is a wireless router but that also delivers integrated services at broadband speeds to small offices and remote workers.
From Wireless Router to Integrated Services Network Router
Integrated services network routers from Cisco go beyond the dedicated wireless router.
The Cisco 800 Series Integrated Services Routers are priced and designed specifically for small offices and remote workers. In addition to serving as a third-generation wireless router, the Cisco 800 Series provides such features as:
- Security that's built directly into the wireless router, including content filtering
- Wide-area-network (WAN) connection with multiple access options
- Primary and backup connections on the Cisco 880 wireless router, including 3G and ISDN networks, for business continuity
- Four 10/100 Mbps Fast Ethernet managed switch ports with optional PoE on two switch ports
- Up to 20 Virtual Private Network (VPN) tunnels, for secure remote access
- An integrated access point based on the IEEE 802.11n draft 2.0 wireless network standard that uses MIMO (Multi-Input, Multiple-output) to improve wireless router coverage.
Cisco Router Configuration Tutorial
Acknowledgments
The following sources where extremely useful:
Leinwand, Pinsky, and Culpepper. Cisco Router Configuration. Indianapolis, Indiana: Cisco Press, 1998.
Cisco Systems, Inc., http://www.cisco.com
Disclaimer
This document carries no explicit or implied warranty. Nor is there any guarantee that the information contained in this document is accurate. It is offered in the hopes of helping others, but you use it at your own risk. The author will not be liable for any damages that occur as a result of using this document.
Conventions
Important terms and concepts, when they are introduced, may be displayed in bold. Commands included in the body of the text will be displayed in this font. All names and addresses used in examples are just that, examples, and should not be used on your network. Do not type them in verbatim when configuring your system. Finally, in some examples where the command rquires an IP address as an argument, the IP address may be represented in this way, xx.xx.xx.xx, or aa.bb.cc.dd. You will never actually use these strings when configuring your system. They are mearly a convention of this document to specify that you should substitute the appropriate IP address at that point.
1. What this document covers
There are several methods available for configuring Cisco routers. It can be done over the network from a TFTP server. It can be done through the menu interface provided at bootup, and it can be done from the menu interface provided by using the command setup. This tutorial does not cover these methods. It covers configuration from the IOS command-line interface only. Useful for anyone new to Cisco routers, and those studying for CCNA.
Note that this tutorial does not cover physically connecting the router to the networks it will be routing for. It covers operating system configuration only.
1.1 Reasons for using the command-line
The main reason for using the command-line interface instead of a menu driven interface is speed. Once you have invested the time to learn the command-line commands, you can perform many operations much more quickly than by using a menu. This is basically true of all command-line vs. menu interfaces. What makes it especially efficient to learn the command-line interface of the Cisco IOS is that it is standard across all Cisco routers. Also, some questions on the CCNA exam require you to know command-line commands.
2. Getting started with Cisco
Initially you will probably configure your router from a terminal. If the router is already configured and at least one port is configured with an IP address, and it has a physical connection to the network, you might be able to telnet to the router and configure it across the network. If it is not already configured, then you will have to directly connect to it with a terminal and a serial cable. With any Windows box you can use Hyperterminal to easily connect to the router. Plug a serial cable into a serial (COM) port on the PC and the other end into the console port on the Cisco router. Start Hyperterminal, tell it which COM port to use and click OK. Set the speed of the connection to 9600 baud and click OK. If the router is not on, turn it on.
If you wish to configure the router from a Linux box, either Seyon or Minicom should work. At least one of them, and maybe both, will come with your Linux distribution.
Often you will need to hit the Enter key to see the prompt from the router. If it is unconfigured it will look like this:
Router>
If it has been previously configured with a hostname, it will look like this:
hostname of router>
If you have just turned on the router, after it boots it will ask you if you wish to begin initial configuration. Say no. If you say yes, it will put you in the menu interface. Say no.
2.1 Modes
The Cisco IOS command-line interface is organized around the idea of modes. You move in and out of several different modes while configuring a router, and which mode you are in determines what commands you can use. Each mode has a set of commands available in that mode, and some of these commands are only available in that mode. In any mode, typing a question mark will display a list of the commands available in that mode.
Router>?
2.2 Unprivileged and privileged modes
When you first connect to the router and provide the password (if necessary), you enter EXEC mode, the first mode in which you can issue commands from the command-line. From here you can use such unprivileged commands as ping, telnet, and rlogin. You can also use some of the show commands to obtain information about the system. In unprivileged mode you use commands like, show version to display the version of the IOS the router is running. Typing show ? will diplay all the show commands available in the mode you are presently in.
Router>show ?
You must enter privileged mode to configure the router. You do this by using the command enable. Privileged mode will usually be password protected unless the router is unconfigured. You have the option of not password protecting privileged mode, but it is HIGHLY recommended that you do. When you issue the command enable and provide the password, you will enter privileged mode.
To help the user keep track of what mode they are in, the command-line prompt changes each time you enter a different mode. When you switch from unprivileged mode to privileged mode, the prompt changes from:
Router>
to
Router#
This would probably not be a big deal if there were just two modes. There are, in fact, numerous modes, and this feature is probably indispensable. Pay close attention to the prompt at all times.
Within privileged mode there are many sub-modes. In this document I do not closely follow Cisco terminology for this hierarchy of modes. I think that my explanation is clearer, frankly. Cisco describes two modes, unprivileged and privileged, and then a hierarchy of commands used in privileged mode. I reason that it is much clearer to understand if you just consider there to be many sub-modes of privileged mode, which I will also call parent mode. Once you enter privileged mode (parent mode) the prompt ends with a pound sign (#). There are numerous modes you can enter only after entering privileged mode. Each of these modes has a prompt of the form:
Router(arguments)#
They still all end with the pound sign. They are subsumed within privileged mode. Many of these modes have sub-modes of their own. Once you enter priliged mode, you have access to all the configuration information and options the IOS provides, either directly from the parent mode, or from one of its submodes.
3. Configuring your Cisco Router
If you have just turned on the router, it will be completely unconfigured. If it is already configured, you may want to view its current configuration. Even if it has not been previously configured, you should familiarize yourself with the show commands before beginning to configure the router. Enter privileged mode by issuing the command enable, then issue several show commands to see what they display. Remember, the command show ? will display all the showcommands aavailable in the current mode. Definately try out the following commands:
Router#show interfaces
Router#show ip protocols
Router#show ipv6 protocols
Router#show ip route
Router#show ipv6 route
Router#show ip arp
Router#show ipv6 neighbors
When you enter privileged mode by using the command enable, you are in the top-level mode of privileged mode, also known in this document as "parent mode." It is in this top-level or parent mode that you can display most of the information about the router. As you now know, you do this with the show commands. Here you can learn the configuration of interfaces and whether they are up or down. You can display what IP protocols are in use, such as dynamic routing protocols. You can view the route and ARP tables, and these are just a few of the more important options.
As you configure the router, you will enter various sub-modes to set options, then return to the parent mode to display the results of your commands. You also return to the parent mode to enter other sub-modes. To return to the parent mode, you hit ctrl-z. This puts any commands you have just issued into affect, and returns you to parent mode.
3.1 Global configuration (config)
To configure any feature of the router, you must enter configuration mode. This is the first sub-mode of the parent mode. In the parent mode, you issue the command config.
Router#config
Router(config)#
As demonstrated above, the prompt changes to indicate the mode that you are now in.
In connfiguration mode you can set options that apply system-wide, also refered to as "global configurations." For instance, it is a good idea to name your router so that you can easily identify it. You do this in configuration mode with the hostname command.
Router(config)#hostname ExampleName
ExampleName(config)#
As demonstrated above, when you set the name of the host with the hostname command, the prompt immediately changes by replacing Router with ExampleName. (Note: It is a good idea to name your routers with an organized naming scheme.)
Another useful command issued from config mode is the command to designate the DNS server to be used by the router:
ExampleName(config)#ip name-server aa.bb.cc.dd
ExampleName(config)#ctrl-Z
ExampleName#
This is also where you set the password for privileged mode.
ExampleName(config)#enable secret examplepassword
ExampleName(config)#ctrl-Z
ExampleName#
Until you hit ctrl-Z (or type exit until you reach parent mode) your command has not been put into affect. You can enter config mode, issue several different commands, then hit ctrl-Z to activate them all. Each time you hit ctrl-Z you return to parent mode and the prompt:
ExampleName#
Here you use show commands to verify the results of the commands you issued in config mode. To verify the results of the ip name-server command, issue the command show host.
3.2 Configuring Cisco router interfaces
Cisco interface naming is straightforward. Individual interfaces are referred to by this convention:
media type slot#/port#
"Media type" refers to the type of media that the port is an interface for, such as Ethernet, Token Ring, FDDI, serial, etc. Slot numbers are only applicable for routers that provide slots into which you can install modules. These modules contain several ports for a given media. The 7200 series is an example. These modules are even hot-swapable. You can remove a module from a slot and replace it with a different module, without interrupting service provided by the other modules installed in the router. These slots are numbered on the router.
Port number refers to the port in reference to the other ports in that module. Numbering is left-to-right, and all numbering starts at 0, not at one.
For example, a Cisco 7206 is a 7200 series router with six slots. To refer to an interface that is the third port of an Ethernet module installed in the sixth slot, it would be interface ethernet 6/2. Therefor, to display the configuration of that interface you use the command:
ExampleName#show interface ethernet 6/2
If your router does not have slots, like a 1600, then the interface name consists only of:
media type port#
For example:
ExampleName#show interface serial 0
Here is an example of configuring a serial port with an IP address:
ExampleName#config
ExampleName(config)#interface serial 1/1
ExampleName(config-if)#ip address 192.168.155.2 255.255.255.0
ExampleName(config-if)#ipv6 address fe80::230:1bff:fe80:b8ea/64
ExampleName(config-if)#ipv6 enable
ExampleName(config-if)#no shutdown
ExampleName(config-if)#ctrl-Z
ExampleName#
Then to verify configuration:
ExampleName#show interface serial 1/1
Note the no shutdown command. An interface may be correctly configured and physically connected, yet be "administratively down." In this state it will not function. The command for causing an interface to be administratively down is shutdown.
ExampleName(config)#interface serial 1/1
ExampleName(config-if)#shutdown
ExampleName(config-if)#ctrl-Z
ExampleName#show interface serial 1/1
In the Cisco IOS, the way to reverse or delete the results of any command is to simply put no infront of it. For instance, if we wanted to unassign the IP address we had assigned to interface serial 1/1:
ExampleName(config)#interface serail 1/1
ExampleName(config-if)#no ip address 192.168.155.2 255.255.255.0
ExampleName(config-if)ctrl-Z
ExampleName#show interface serial 1/1
Configuring most interfaces for LAN connections might consist only of assigning a network layer address and making sure the interface is not administratively shutdown. It is usually not necessary to stipulate data-link layer encapsulation. Note that it is often necessary to stipulate the appropriate data-link layer encapsulation for WAN connections, such as frame-relay and ATM. Serial interfaces default to using HDLC. A discussion of data-link protocols is outside the scope of this document. You will need to look up the IOS command encapsulation for more details.
3.3 Configuring Cisco Routing
IP routing is automatically enabled on Cisco routers. If it has been previously disabled on your router, you turn it back on in config mode with the command ip routing.
ExampleName(config)#ip routing
ExampleName(config)#ctrl-Z
To enable IPv6 routing, use the command ipv6 unicast-routing.
ExampleName(config)#ipv6 unicast-routing
ExampleName(config)#ctrl-Z
There are two main ways a router knows where to send packets. The administrator can assign static routes, or the router can learn routes by employing a dynamic routing protocol.
Static routes are generally used in very simple networks or in particular cases that necessitate their use. To create a static route, the administrator tells the router operating system that any network traffic destined for a specified network layer address should be forwarded to a similiarly specified network layer address. In the Cisco IOS this is done with the ip route and ipv6 route commands.
ExampleName#config
ExampleName(config)#ip route 172.16.0.0 255.255.255.0 192.168.150.1
ExampleName(config)#ctrl-Z
ExampleName#show ip route
ExampleName#config
ExampleName(config)#ipv6 route fe80::230:1bff:fe80::/64 fe80::230:1bff:fe80::1
ExampleName(config)#ctrl-Z
ExampleName#show ipv6 route
Two things to be said about this example. First, the packet destination address must include the subnet mask for that destination network. Second, the address it is to be forwarded to is the specified addres of the next router along the path to the destination. This is the most common way of setting up a static route, and the only one this document covers. Be aware, however, that there are other methods.
Dynamic routing protocols, running on connected routers, enable those routers to share routing information. This enables routers to learn the routes available to them. The advantage of this method is that routers are able to adjust to changes in network topologies. If a route is physically removed, or a neighbor router goes down, the routing protocol searches for a new route. Routing protocols can even dynamically choose between possible routes based on variables such as network congestion or network reliability.
There are many different routing protocols, and they all use different variables, known as "metrics," to decide upon appropriate routes. Unfortunately, a router needs to be running the same routing protocols as its neighbors. Many routers can, however, run mutliple protocols. Also, many protocols are designed to be able to pass routing information to other routing protocols. This is called "redistribution."
Routing protocols are a complex topic and this document contains only this superficial description of them. There is much to learn about them, and there are many sources of information about them available. An excelent source of information on this topic is Cisco's website, http://www.cisco.com.
3.4 IPv6 configuration with IOS
This is a seperate section because IPv6 is new to most people, and they will be looking specifically for information about configuring IPv6. Examples of configuring IPv6 are included throughout the document, however, alongside IPv4. That is a more accurate reflection of how you will work with IPv6 on a day-to-day basis. Once the newness of IPv6 passes, it will be one more piece in the familiar puzzle.
The important concept to understand when configuring IPv6 is that IPv4 and IPv6 exist in parrallel. One is not a replacement for the other, at least not in the way it is treated by the operating system. A term for this is dual stack. An interface can have an IPv4 address and no IPv6 address. Or an IPv6 address and no IPv4 address. Or both an IPv4 address and an IPv6 address. Examples:
IPv4 only
!
interface FastEthernet0/0
ip address 192.168.1.138 255.255.255.0
!
IPv6 only
!
interface FastEthernet0/0
ipv6 address fe80::230:1bff:fe80::/64
ipv6 enable
!
IPv4 and IPv6
!
interface FastEthernet0/0
ip address 192.168.1.138 255.255.255.0
ipv6 address fe80::230:1bff:fe80::/64
ipv6 enable
!
Notice that there are seperate but similiar commands for IPv4 and IPv6. To assign an IPv4 address,
ExampleName(config-if)#ip address 192.168.1.138 255.255.255.0
To assign an IPv6 address,
ExampleName(config-if)#ipv6 address fe80::230:1bff:fe80::/64
There are some bigger differences between IPv4 and IPv6 IOS commands. For example, the IPv6 equivilant of show ip arp, is show ipv6 neighbors.
3.5 Saving your Cisco Router configuration
Once you have configured routing on the router, and you have configured individual interfaces, your router should be capable of routing traffic. Give it a few moments to talk to its neighbors, then issue the commands show ip route and show ip arp. There should now be entries in these tables learned from the routing protocol.
If you turned the router off right now, and turned it on again, you would have to start configuration over again. Your running configuration is not saved to any perminent storage media. You can see this configuration with the command show running-config.
ExampleName#show running-config
You do want to save your successful running configuration. Issue the command copy running-config startup-config.
ExampleName#copy running-config startup-config
Your configuration is now saved to non-volatile RAM (NVRAM). Issue the command show startup-config.
ExampleName#show startup-config
Now any time you need to return your router to that configuration, issue the command copy startup-config running-config.
ExampleName#copy startup-config running-config
3.6 Example Cisco Router configuration
Router>enable
Router#config
Router(config)#hostname N115-7206
N115-7206(config)#interface serial 1/1
N115-7206(config-if)ip address 192.168.155.2 255.255.255.0
N115-7206(config-if)ipv6 address fe80::230:1bff:fe80:b8ea/64
N115-7206(config-if)ipv6 enable
N115-7206(config-if)no shutdown
N115-7206(config-if)ctrl-z
N115-7206#show interface serial 1/1
N115-7206#config
N115-7206(config)#interface ethernet 2/3
N115-7206(config-if)#ip address 192.168.150.90 255.255.255.0
N115-7206(config-if)#no shutdown
N115-7206(config-if)#ctrl-z
N115-7206#show interface ethernet 2/3
N115-7206#config
N115-7206(config)#ip name-server 172.16.0.10
N115-7206(config)#ctrl-z
N115-7206#ping archie.au
N115-7206#config
N115-7206(config)#enable secret password
N115-7206(config)#ctrl-z
N115-7206#copy running-config startup-config
N115-7206#exit
4. Troubleshooting your Cisco router
Inevitably, there will be problems. Usually, it will come in the form of a user notifying you that they can not reach a certain destination, or any destinattion at all. You will need to be able to check how the router is attempting to route traffic, and you must be able to track down the point of failure.
You are already familiar with the show commands, both specific commands and how to learn what other show commands are available. Some of the most basic, most useful commands you will use for troubleshooting are:
Router#show interfaces
Router#show ip protocols
Router#show ipv6 protocols
Router#show ip route
Router#show ipv6 route
Router#show ip arp
Router#show ipv6 neighbors
4.1 Testing connectivity
It is very possible that the point of failure is not in your router configuration, or at your router at all. If you examine your router's configuration and operation and everything looks good, the problem might be be farther up the line. In fact, it may be the line itself, or it could be another router, which may or may not be under your administration.
One extremely useful and simple diagnostic tool is the ping command. Ping is an implementation of the IP Message Control Protocol (ICMP). Ping sends an ICMP echo request to a destination IP address. If the destination machine receives the request, it responds with an ICMP echo response. This is a very simple exchange that consists of:
Hello, are you alive?
Yes, I am.
ExampleName#ping xx.xx.xx.xx
If the ping test is successful, you know that the destination you are having difficulty reaching is alive and physically reachable.
If there are routers between your router and the destination you are having difficulty reaching, the problem might be at one of the other routers. Even if you ping a router and it responds, it might have other interfaces that are down, its routing table may be corrupted, or any number of other problems may exist.
To see where packets that leave your router for a particular destination go, and how far, use the trace command.
ExampleName#trace xx.xx.xx.xx
It may take a few minutes for this utility to finish, so give it some time. It will display a list of all the hops it makes on the way to the destination.
4.2 debug commands
There are several debug commands provided by the IOS. These commands are not covered here. Refer to the Cisco website for more information.
4.3 Hardware and physical connections
Do not overlook the possibility that the point of failure is a hardware or physical connection failure. Any number of things can go wrong, from board failures to cut cables to power failures. This document will not describew troubleshooting these problems, except for these simple things.
Check to see that the router is turned on. Also make sure that no cables are loose or damaged. Finally, make sure cables are plugged into the correct ports. Beyond this simple advice you will need to check other sources.
4.4 Out of your control
If the point of failure is farther up the line, the prolem might lie with equipment not under your administration. Your only option might be to contact the equipment's administrator, notify them of your problem, and ask them for help. It is in your interest to be courtious and respectful. The other administrator has their own problems, their own workload and their own priorities. Their agenda might even directly conflict with yours, such as their intention to change dynamic routing protocols, etc. You must work with them, even if the situation is frustrating. Alienating someone with the power to block important routes to your network is not a good idea.
5. References
Leinwand, Pinsky and Culpepper Cisco Router Configuration. Indianapolis, Indiana: Cisco Press, 1998.
Cisco Systems, Inc., http://www.cisco.com
Apple Networks
This document describes the AppleTalk and LocalTalk network as implemented on the Apple Macintosh. It describes the various parts of the Apple network like: AFP, ASP, ZIP, ADSP, ATP, AEP, NBP, RTMP, DDP, LLAP, ELAP, TLAP, LocalTalk, EtherTalk and TokenTalk
Introduction
When Apple Computer introduced the Apple Macintosh in 1984 it had a build in networking facility that was called AppleTalk. It consists of two major parts: the protocol-stack called AppleTalk and the physical network called LocalTalk. The LocalTalk part can be exchanged by e.g. Ethernet, Apple calls this EtherTalk, or Token Ring, which is then called TokenTalk.
Next to these there is also a cheap telephone-wire-network called PhoneNET from Farallon Computing and Apple also has a telephone wire system called LocalTalk RJ-11.
Currently there are two flavours of the AppleTalk protocol-stack:
- AppleTalk Phase 1
- AppleTalk Phase 2 (1989, available from system 7.0)
Old units with Phase 1 can not communicate with Phase 2 units, or atleast can not use all the benefits of Phase 2. The Phase 2 adds extended addressing, dynamic node addressing, distributed name service, AppleTalk zones and best routing algorithms. In this document only Phase 2 is taken into account.
Addressing
The AppleTalk addressing scheme has three portions: a Network number, a Node ID, and a Socket number.
Next to this AppleTalk also knows a feature called Zone name. Every node (workstation, server, router) is part of a zone. A zone is a group of stations that logically fit together although they do not need to be in the same room. The system administrator has the possibility to control such a group instead of using controls on a per person basis.
The addressing of a node can be done manually or automatically. This means you can manually set the node ID, but you can also leave it to the network to take care of that. When the automatic feature is used a node will pick a random ID and then checks it with the network to see if it's free.
The node address is written down in two parts. The first part is the network address and the second part in the node address on that network. Both addresses are separated by a dot (.)
The Node ID is an eight bit number which results in 254 (0 and 255 are the broadcast addresses) nodes on one network.
The Network ID is an eight bit number for AppleTalk Phase 1 and a sixteen bit number for AppleTalk Phase 2 which results in respectively 254 and 65534 possible networks.
To identify an application on a node (you could have several applications running on one node) there is another address to address that application on a node. This address is called a socket, which is also an eight bit number with a maximum of 254 sockets on a single node.
Another feature within AppleTalk networks is the use of zones. The zone-name is a by the system administrator choosen name for a group of users. This way the administrator can set rules for this group without having to set rules for every user. Logical groups would be: sales, marketing, etc.
Devices on a network
All devices that are addressable are called Nodes (workstations, file-servers, printers, routers). However there are some special devices in a network which are called routers. The various types of routers are:
- Seed Routers
- Broadcast information about network numbers and zone names
- Nonseed Routers
- Learn the network through information received by Seed Routers
The Apple network compared to OSI
| 7 | Application Layer | AppleShare (files, printers, PCs) | |
| 6 | Presentation Layer | AppleTalk Filing Protocol (AFP), Printer Access Protocol (PAP) | |
| 5 | Session Layer | AppleTalk Session Protocol (ASP), Zone Protocol (ZIP), AppleTalk Data Stream Protocol (ADSP) | |
| 4 | Transport Layer | AppleTalk Transport Protocol (ATP), AppleTalk Echo Protocol (AEP), Name-Binding Protocol (NBP), Routing Table Maintenance Protocol (RTMP) | |
| 3 | Network Layer | Datagram Delivery Protocol (DDP) | |
| 2 | LLC | Data Link Layer | LocalTalk Link-Access Protocol (LLAP), Ethernet Link-Access Protocol (ELAP), Token ring Link-Access Protocol (TLAP), Other Link-Access Protocols |
| MAC | LocalTalk, EtherTalk, TokenTalk, or other Network Topologies | ||
| 1 | Physical Layer | STP, UTP, Coax, Fiber | |
Layer 7
AppleShare is incorporated in the Macintosh OS. It is a client/server protocol between an AppleShare server and a client (workstation).
Layer 6
AFP allows workstations on an AppleTalk network to access files on AppleShare servers. It makes remote harddisks look like local ones. It is not a common used protocol because the native file system commands allow users to access an server. There is no server-based interface.
PAP stands for Printer Access Protocol and maintaines print services.
Layer 5
ASP is responsible for setting up and maintaining sessions between workstations and the server. The protocol is asymmetrical (completely controlled by the client). A more commanly used protocol for this is ADSP.
ZIP is the protocol that provides the higher layers with zone information. Zones are used in a Macintosh network to identify groups of users, like sales, marketing, etc.
ADSP is a connection oriented protocol that has the same function as ASP. It uses sockets to exchange full-duplex data streams over an AppleTalk network. In contrast with ASP, ADSP is symmetrical protocol. This means that the socket clients have equal control over the ADSP session.
Layer 4
ATP is a protocol that exchanges commands between socket clients. ATP provides reliable delivery of packets. It takes care of retransmissions and puts arrived packets in the correct order.
AEP is a socket that resides on every client and listens to the network. If an echo packet arrives it immediatly sends back the packet to the sender. Those familiar with TCP/IP will recognize this feature from the Ping utility.
NBP is, as the name implies, a way to bind names to addresses. The binding can be with nodes and applications (sockets). All AppleTalk applications use NBP to make their services known throughout the network.
RTMP is used by AppleTalk routers to maintain their routing tables. Each workstation contains a small part of the RMTP called the RMTP stub. This portion is used by DDP to determine the network number and network ID.
Layer 3
DDP is a connectionless protocol that is responsible for the transfer of datagrams between sockets. It doesn't care about reliability, correct order, nor does it care about the transport medium.
Layer 2 LLC
The LAPs make it possible to use AppleTalk over different networks. For each network topology there is a different LAP.
LocalTalk; The Network
Layer 2
LocalTalk uses a CSMA/CA protocol to make use of the serial bus that the network is. Since all computers are daisy-chained to eachother there is a need for accessing the shared bus. CSMA/CA stands for Carrier Sense Multiple Access with Collision Avoidance. Which means that every stations listens to the bus to see if it's free. If it's free every station waits for a random time and then starts transmitting the data it has to send. The change of a collision is minimized by the random delay timer. When a collision does occur, all sending stations back off and the random delay timer starts again.
The frame format used is SDLC (Synchronous Data Link Control).
The interface between the MAC-layer and Layer 1 is AAUI (Apple Attachment Unit Interface). This connector can be used to connect different physical interface tranceivers, like 10Base-T, 10Base-2 or 10Base-5. The electrical characteristics and functions are identical to the AUI connector defined in the IEEE 802.3.
| Male | Female |
|---|---|
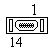 | 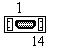 |
The card always has a male connector with the following pinning:
| Pin | Signal | Description |
|---|---|---|
| 1 | FN Pwr | +12 Vdc @ 175 mA or +5 Vdc @ 420 mA |
| 2 | DI-A | Data In circuit A |
| 3 | DI-B | Data In circuit B |
| 4 | VCC | Voltage Common |
| 5 | CI-A | Control In circuit A |
| 6 | CI-B | Control In circuit B |
| 7 | +5V | +5 Vdc (from host) |
| 8 | +5V | Secondary +5 Vdc (from host) |
| 9 | DO-A | Data Out circuit A |
| 10 | DO-B | Data Out circuit B |
| 11 | VCC | Secondary Voltage Common |
| 12 | NC | Not Connected |
| 13 | NC | Not Connected |
| 14 | FN Pwr | Secondary +12 Vdc @ 175 mA or +5 Vdc @ 420 mA |
| Shell | Protective GND | Protective Ground |
Layer 1
Electrical
The signalling used is EIA modified RS422. With a speed of 230k4 bps. The signal encoding used FMO (bi-phase space).
Cabling & Connectors
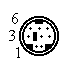
LocalTalk is the standard cabling method used with AppleTalk networks. The topology is a serial bus structure with transformer isolation. To connect a Macintosh to the network you connect the 8-pin mini-DIN printer port to a LocalTalk adapter. From these adapters you daisy-chain adapters to eachother through a shielded twisted pair cable with mini-DIN 3 male connectors. The maximum cable length is 1000 ft/ 330 mtr. The adapters are auto-terminating so no terminators are needed.
| Mini-DIN8 | Mini-DIN3 | RJ11 | |||
|---|---|---|---|---|---|
| Male | Female | Male | Female | Male | Female |
 | 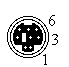 | 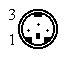 | 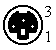 | 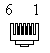 | 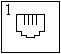 |
EtherTalk
EtherTalk is AppleTalk over Ethernet. Apple uses SNAP, SubNetwork Access Protocol on the LLC sub-layer.
TokenTalk
TokenTalk is AppleTalk over Token Ring.


No comments:
Post a Comment